In this article I will explain what a backdoor is and what types of backdoors currently exist. In addition, how to create a backdoor will also be explained in the second part. At the end of the article there is a backdoor fix that you can try to secure your Linux server.
What is Backdoor?
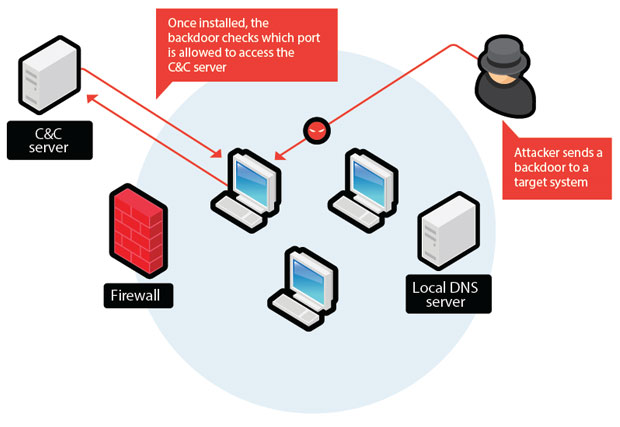
Understanding Backdoor in a software or computer system is an undocumented portal. This portal allows administrators to log in to the system to perform troubleshooting or maintenance.
However, the term backdoor is more often used in the context of hacking. In hacking, a backdoor is a secret portal used by hackers and intelligence agencies to gain unauthorized access to software, websites, or computer systems.
Backdoor itself does have several meanings. But the popular definition of Backdoor usually refers to an access point that is legally embedded in a system or software program for remote administration.
Usually, such undocumented backdoors are used to maintain software or systems. Some administrative backdoors are indeed called usernames and passwords that are hardcoded and cannot be changed, although some use credentials that can be changed.
Usually, the system owner is not necessarily aware of a backdoor. The one who usually knows for sure is the software maker. The admin backdoor that is built-in actually makes a system or software vulnerable to hackers who want to gain access to the system or data.
Attackers can install their own backdoor on the targeted system. That way, they can freely enter and go to a system.
Not only that, they can also access the system remotely. Malware that is installed specifically for this is usually called a remote access Trojan (RAT) and can be used to install other malware onto a system or data.
Backdoor became famous after Edward Snowden leaked the documents of the American National Security Agency (NSA) in 2013.
From this document, Edward Snowden leaked that the NSA asked electronics companies to install backdoors on their products, especially to companies that use encryption systems. This secret backdoor allows intelligence agencies to read the system and data on the product.
One of the most controversial backdoor cases was the NSA’s attempt to weaken an encryption algorithm known as the NIST SP800-90 Dual Ec Prng so that data encrypted with that algorithm could be opened by the NSA.
Why Are Backdoors Dangerous?

As explained above, backdoors have become a hot topic of discussion because of the dangers of providing dark access. But there are a few more things that make backdoors considered dangerous.
-
DDoS (Distributed Denial of Service) attacks
One of the most serious threats is a DDos attack or Distributed Denial of Service. This attack occurs when a hacker makes the server send various packets to one destination.
This attack makes a machine or network unable to work properly because the amount of traffic is too high.
Denial of service becomes distributed when there are several machines in the world participating in the attack at the same time. In this case, hackers will have backdoors in many systems that can be used to perform DDoS. Servers that then participate in the attack may be blacklisted in the end.
-
Malware Distribution
By installing a backdoor on a web server, a hacker can distribute malware to website visitors. The malware that is commonly distributed is ransomware or adware which hackers can take advantage of.
If your website is hit by this attack, your website will be blocked directly by browsers such as Chrome and Opera.
-
Data Theft
This is the most frequently discussed backdoor hazard. In this case, the backdoor would be a way for hackers to access the web server from time to time to steal important information from the server, such as for example customer data or use the server as a turning point to steal from adjacent networks.
Hackers usually do this clandestinely. In fact, you may not notice anything wrong with your server at all.
Finding such backdoors is difficult, not only because they can use advanced techniques, but because you may not even know they are there.
One way to find such backdoors is to periodically check the appropriate logs. Also, securing the server is the best way to prevent hacking.
How to Avoid Backdoors?
There are several ways you can do to keep your website and device safe from backdoors.
-
Enable firewall to prevent backdoor
By activating the website firewall regardless of device, you will block unauthorized users (or users without permission) so that they cannot retrieve data from your website and device.
-
Be careful with open-source software
If you choose to use open-source software, make sure that the software you use gets a good rating and is said to be safe. Indeed, this open-source software is official from the brand, but there are many hidden backdoors that can steal information or even control your system.
Hackers also know that changing software code can give them backdoor access to other computers or networks.
-
Use anti-virus software
Make sure that your anti-virus is updated to the latest version. Also, make sure that your computer’s operating system and the programs on your laptop are updated to the latest version. That way, they can dodge attacks.
-
Be careful with the emails you receive
Even if the email you receive is from someone you know, hackers can pretend to be that person so they can gain access to your laptop.
Look for an anti-virus that can do an email scan and first scan every attachment before you open the email so that you are not exposed to backdoors or other attacks.
Backdoor Function
The most widely used backdoor function is to enter the system without having to go through the authentication mechanism. This function is widely used by programmers to get into the system they develop. Due to the system that is in the process of development sometimes there are still many problems such as sudden stops and other bugs.
Here are some other backdoor functions .
-
Retrieve website access rights
What is a backdoor to take website access rights? Backdoors are currently widely distributed in various applications and features used on a website. The goal is to gain access to the website. Once logged in, it depends on the backdoor maker or the so -called hacker. Because, when you can get into the website system, then hackers can do anything.
There are several ways that can be used to insert a backdoor into a website, such as through themes, plugins , upload folders , wp-config , and include folders . Most of these backdoors are even entered by the victim himself by accident.
-
Retrieves server/computer permissions
Another thing that is quite dangerous is when hackers successfully put a backdoor into the server (could be a personal device). When the backdoor has entered into a victim’s system, hackers can access to all folders in the device. Not infrequently hackers also commit data theft using this method.
Unlike how to take website access rights, inserting a backdoor into a device is mostly through an application installed by the victim. These applications are generally not known as backdoors , because hackers give these applications the name of the program that is reasonable and even that the victim wants to install.
The purpose backdoor on a web server is used to perform malicious activity, including:
- Data theft
- Server hijacking
- Damages the website
- Put a virus on website visitors
- Performing Distributed Denial of Service (DDoS) attacks
Backdoor type
The types of backdoors are seen from the type.
- Web Shell Backdoor
Web Shell Backdoor is one way to obtain a backdoor (entrance) through a web shell. What is a web shell? A web shell is a type of command text contained on a website page that can be used to gain access to the system by executing certain programs.
- System Backdoor
System Backdoors are the most popular type of backdoor of all types of backdoors . This type is included as the main target in doing backdoor . Because it provides flexibility and stability compared to web shell backdoor .
Steps to Finding a Backdoor
For the security of your system, especially online -based. There are several things you can do to find and prevent possible backdoors attacking your system. In this section I will discuss about the ways that can be done to handle backdoor on systems that use the Linux operating system in particular.
Things to Prepare
- A client computer that can be used to access a server or web hosting.
Overcoming Backdoor
Overcoming backdoors in web hosting
On web hosting there are several things that can be done to clean the backdoor. Here are some checks that can be done for backdoor handling.
- Unused themes are best removed and use original and trusted themes.
- Check the .htaccess file , making sure there are no redirect scripts .
- Check the wp-config.php file so that it is the same as the wp-config-sample.php file in the configuration.
Find Files Containing Backdoor
This step is sometimes useful for handling post -attack on web hosting servers. The goal is to find out if there are still scripts embedded in a file in one of the folders. The problem is that there are a lot of folders and files stored. Ranging from hundreds of megabytes to a few gigabytes .
One way you can find a snippet of code in one of the server files is to use the command text. On Linux there is a grep command that can be used to find snippets of script in a file.
Grep is already in every Linux so there is no need to install again. As for the website file that you want to check, it must be downloaded first.
Finding the Passtrhu Command Line Using Linux
The following command line is used to search for all folders and files contained in public_html that contain passwords .
$ grep -Rn “passthru *(” public_html/
If you want to save the results of a search into a file, eat can use the following command.
$ grep -Rn “passthru *(” public_html/ >> hasil.txt
Finding the Passtrhu Command Line Using Windows
If you are using a Windows operating system, there are also commands that can be used to check lines of code. If Linux uses Grep then Windows uses Findstr .
$ findstr /r /s /n /c: ”passthru *(” *. *
Both of these methods are one example of several things that can be done to deal with backdoor issues.
Closing
In this article has been explained about what is a backdoor and how the backdoor works. Although simple, backdoors are tools that can be a fatal mistake for system administrators. Because it can forcibly take over access rights to the system.
There are several precautions that can be taken to deal with backdoors. But the simplest thing you can do is to minimize the use of untrusted files or folders. Because sometimes on some themes, for example websites, there are some themes that are embedded backdoor in it.
Hopefully this article on what a backdoor is can be useful. After getting information about backdoors , here are some articles that you may be interested in reading as well.
