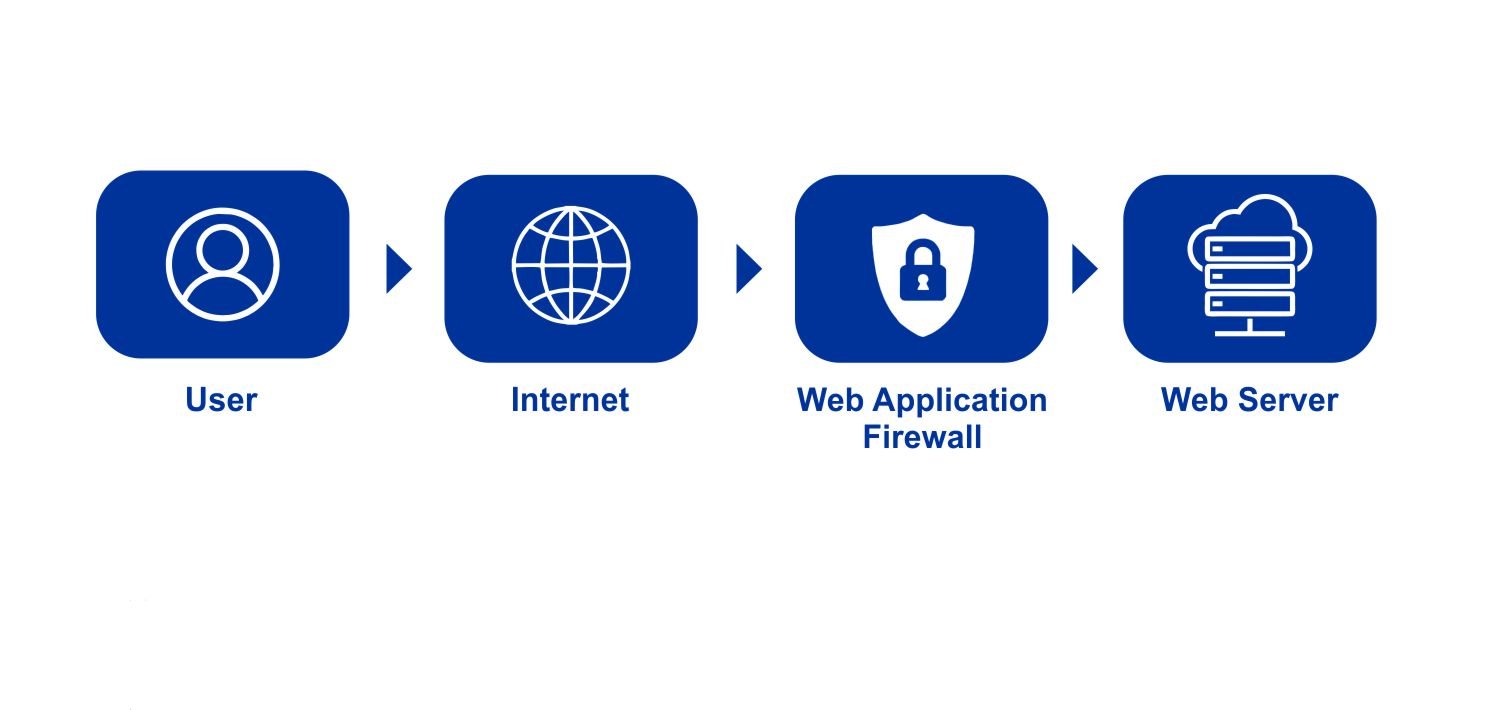
Web Application Firewall (WAF) is a firewall that monitors, filters, and blocks data coming from the client to a website or web application. A Web Application Firewall can be network-based, host-based or cloud-based, and is sometimes used via a reverse proxy in front of a website or application.
As a network tool, server plugin or cloud service, WAF examines every data to analyze Layer 7 web application logic and filter out malicious traffic that can damage websites. WAF is a security that is quite commonly used by companies to protect websites from exploits, malware, and other threats.
Through these safeguards, Web Application Firewall (WAF) can detect and quickly secure websites from even the most dangerous threats, which even traditional firewalls such as IDSes and IPSes cannot.
WAF is usually very useful for companies that provide their products or services on the internet such as e-commerce, online banking, and others.
Web Application Firewall vs Firewall
Firewall is a broad term for firmware that protects a computer network by filtering incoming data. Within these broad terms, there are several categories that are differentiated based on what protection they provide.
Meanwhile, Web Application Firewall (WAF) is another category of firewall and is distinguished by how specifically WAF filters data.
WAF itself is unique because it only focuses on web-based attackers at the application layer, where other types of firewalls cannot fight attacks like this. Web Application Firewall (WAF) is similar to a proxy firewall, but with a specific focus on Layer 7 application logic.
How Web Application Firewall (WAF) works?
Web Application Firewall (WAF) analyzes requests from Hypertext Transfer Protocol (HTTP) and applies all the rules that define which parts are correct or suspicious.
The main parts of HTTP that WAF analyzes are GET and POST requests. GET requests are used to receive data from the server, while POST requests are used to send data to the server.
WAF uses three approaches to analyze and filter content from HTTP. You can listen to it below:
Whitelisting :
Whitelisting means WAF will reject all requests by default and only allow requests that are already trusted. Usually there is already an IP address provided and it is known to be secure.
Whitelisting is an easier way than blacklisting. However, the drawback of whitelisting is the possibility of blocking traffic either accidentally. Although it can be very efficient, sometimes using whitelisting becomes less accurate.
Blacklisting :
Blacklisting by default will leave data and use certain presets to block malicious web traffic or web applications. Simply put, blacklisting is the use of certain rules that can indicate a danger.
Blacklisting is more appropriate for public websites because it receives a lot of traffic from unfamiliar IP addresses, and it is not known whether it is malicious or good traffic.
The disadvantages of blacklisting are that it takes more effort to use it, and must have more information to filter data based on specific information.
Hybrid security :
This model uses both whitelisting and blacklisting elements.
Whichever model you use for WAF, the real hard job is to analyze HTTP interactions and destroy malicious traffic before it hits your server.
Types of Web Application Firewall (WAF)
Network-based WAFs are usually hardware-based and can reduce latency because they are installed locally and near applications. Most network-based WAF vendors allow replicating rules and settings across their equipment, allowing users to deploy and configure at scale.
The disadvantage of this type of WAF is the cost because you will be asked for money in advance, then costs for operational maintenance.
Host-based WAF can be fully integrated into the application code itself. The advantages of implementing host-based WAF are low costs and ease of customization.
However, this type can be difficult because it requires an application library and relies on a local server to work effectively.
Therefore, more employees are needed, including developers, systems analysts, and possibly DevOps / DevSecOps as well.
Cloud-based WAF offers a cheaper solution for companies that want minimal resources for Web Application Firewall (WAF) management. Cloud WAF is easier to deploy and available on a usage or subscription basis.
Sometimes it just takes a simple domain system or proxy change to redirect app traffic. While it may worry you to have to entrust your company’s traffic to third parties, namely WAF vendors, this method allows your application to be protected across a wide spectrum of hosting locations.
In addition, WAF vendors must already have the latest security updates and be able to identify the latest threats as well.
Web Application Firewall (WAF) Benefits
Web Application Firewall (WAF) has many advantages over other traditional firewalls as it offers better visibility of sensitive data from the HTTP layer. WAF can prevent attacks at the application layer that would normally bypass traditional firewalls.
- Attack cross-site scripting (XSS) allows attackers to inject and execute malicious scripts in another user’s browser.
- A structured query language (SQL) attack could compromise any application that uses a SQL database and could allow attackers to access and potentially modify sensitive data.
- Web session hacking can allow attackers to hijack a session ID and impersonate an authorized user. The session ID is usually stored in a cookie or Uniform Resource Locator (URL).
- A distributed denial-of-service (DDoS) attack can make a network so full of traffic that it cannot serve users. Both firewall and WAF networks can actually control this kind of attack, but they do it differently.
In addition to the above benefits, Web Application Firewall (WAF) is also able to maintain web-based applications without having to access the source code.
Although host-based WAF is integrated with application code, a cloud-hosted Web Application Firewall (WAF) is capable of maintaining applications without needing to have access.
In addition, Web Application Firewall (WAF) cloud is also easy to deploy and set up so users can quickly customize settings to adapt to new attacks.