Getting to Know the Basic Iptables Commands on Linux for beginner . This time Matob will only discuss the basics of iptables on GNU/Linux. Iptables itself is a firewall rule that is used to regulate the entry and exit of traffic on the network on the Linux system that we use. In short, iptables is a data traffic controller on the GNU/Linux system that we use.
Since the mid 90’s Linux has inserted a new feature, namely the existence of a firewall. This technology has undergone several changes (the previous generation was known as ipfwadm or ipchains) and now what we know as packet filtering is iptables. Rules or parameters that can be used on Iptables itself are the same in all distributions. So even if you are using a Debian family distro, a RHELL family distro, or another distro, the commands or options are the same.
Rule Table in IPtables
- Filter – Specifies the packet to be DROP, LOG, ACCEPT, or REJECT.
- NAT – Translate (change) the origin or destination address of a packet.
- Mangle – Performs smoothing (mangle) on data packets such as TTL, TOS, and MARK.
Each table above has rules or rules called chains . The filter has 3 chains:
- FORWARD: Performs a packet filter that will be forwarded from one NIC to another NIC as a function on a router
- INPUT: Performs a packet filter intended for the firewall.
- OUTPUT: Performs a packet filter that will exit the firewall.
NAT has 3 chains:
- PRE-ROUTING: Used to translate addresses before the routing process occurs, ie changing the destination IP of the data packet is usually called Destination NAT or DNAT.
- POST-ROUTING: Used to translate addresses after the routing process occurs, namely changing the source IP of the data packets, usually called Source NAT or SNAT.
- OUTPUT: Used to translate the address of data packets coming from the firewall itself.
Mangle has 5 chains: Mangle itself has 5 chains, namely PREROUTING, POSTROUTING, INPUT, OUTPUT, FORWARD. All chains are assigned to TCP Packet Quality of Service before the routing process is executed.
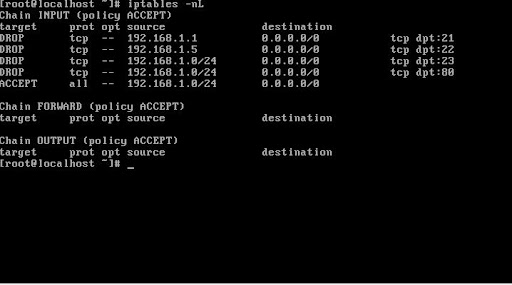
COMMAND
Commands and rules installed in iptables (firewall) have conditions. Basically iptables on a computer is considered an IP TABLE according to its name. The system will only run the existing rules in the table. While the existing rules in iptables can also be deleted or replaced with other rules. Here are some commands for adding, deleting and similar operations that will be treated against the rule. List of Commands with description
- -A or –append — Add a rule
- -D or –delete — Deletes the rule
- -R or –replace — Replacing rule
- -L or –list — Displays a list of iptables
- -F or –flush — Clear iptables list/empty
- -I or –insert — Insert rule
- -N or –new-chain — Add a new chain
- -X or –delete-chain — Deletes a chain
- -P or –policy — Provide standard rules
- -E or –rename -Provides a name replacement
- -h or –help — Displays the help . facility
PARAMETER
The iptables parameter is used as a necessary complement for the purpose of the rule specification
- -p or –protocol -This parameter specifies the treatment of the protocol.
- -m or –match-option -is similar to –p but the module is used and is free to specify the name of the module to be used and vary it in subsequent commands.
- -s or –source — hostname/ip address.
- -d or –destination — etc. Parameters for specifying the destination of the packet.
- -j or –jump — returns a decision after the data packet matches the rule.
- -i or –in-interface — Enter through the interface (eth0, eth1 etc.).
- -o or –out-interface — alias name of the interface that will send the packet out (in the FORWARD or OUTPUT and POSTROUTING chains).
- -c or –counter — to count packets passing through a rule.
- -n or –numeric — displays numeric output such as hostname or ip or port or network name.
- -v or –verbose — which means to display the information in its entirety.
TARGET
Target is the goal of treatment of the rule. At this target lies the decision, what to do with the data packet, whether to reject it, or forward it or process it first. The following is a list of iptables target tables. The following targets Description
- ACCEPT – The packet chain is received in the rule
- DROP – The packet chain is “dropped”
- REJECT – The packet chain is rejected like DROP
- DNAT – Chain packets in “destination nat” to another address
- SNAT – Packet chain directed to a specific nat source
- REDIRECT – The packet chain is redirected to a specific address and port
- MASQUERADE – Works like SNAT but requires no source
- REJECT – Works like DROP
Examples Case
iptables -I INPUT -s 11.22.33.44/32 -j DROP
In the example above, we add a rule to the INPUT chain to block traffic from ip 11.22.33.44. If the IP accesses our network, the traffic will be dropped immediately.
man iptables
iptables –help
