Why Understanding Tags is Key to Optimizing Website SEO

As a digital marketer, it’s important to understand how search engine optimization (SEO) works. By understanding the basics of SEO, you can create better content and make your website more visible in search engine results pages (SERPs). One essential element of SEO is using the correct tags for your website content. In this blog post, […]
Factors to Consider When Using Mozilla Firefox

Are you confused as to whether to use Mozilla Firefox or not? If so, let us help you. This article will show you factors to consider when using Firefox. You will know why it is better for you. Despite losing its market to a certain level due to the introduction of Chrome, Firefox remains stable […]
Best NFT Reviews by Collectible To

If you are interested in the topic of the latest NFT stuff, we are ready to introduce this below! Look through the list to get acquainted with some of the coolest offers: World Save Ukraine. As you can guess, it is a rather relevant NFT collection. It is a charity project with more than 200 […]
Create Simple Network with Cisco Packet Tracer

Previously I have discussed about How to Configure VLANs in Cisco Packet Tracer With One Switch , now for those of you who are interested in learning about networks, especially on Cisco devices, here are the steps to create a simple network with Cisco packet tracer. Simple network with Cisco packet tracer I will create […]
The Importance of Load Balancing on the Network

Are there any of you who don’t know about Load Balancing? If not, then it’s time for you to visit this website. Because of what? Because this time Matob will review a little about The Importance of Load Balancing on the Network . Keep on reading until it’s finished..! Understanding Load Balancing Load Balancing is a technique to distribute the […]
What is DDNS and How to Create It?

Do you know? The IP address that identifies your device can change. The reason is, the more devices connected to the internet, the more limited the available IP addresses. That’s why your device will get a different IP Address from the internet service provider. Well, this changing IP address is of course troublesome. For example, if you have […]
What is FTP and How to Use It?

File transfer protocol or FTP is an internet protocol that allows users to transfer files between servers over a network with a TCP connection. If you often deal with servers and the world of information technology, of course, the term FTP is already familiar. Because currently FTP is one of the most frequently used transfer […]
What is the function of the PCI slot on the motherboard?
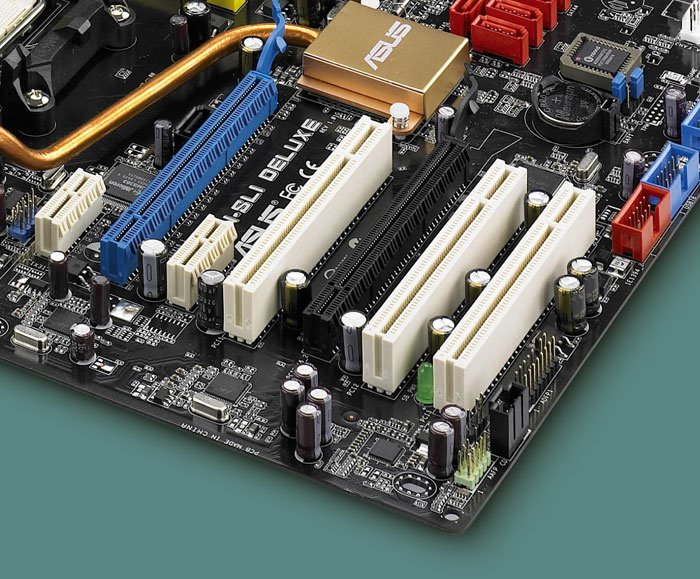
In the following we will explain about what is the function of the PCI slots on the motherboard in detail so that it is hoped that it will provide a deep understanding for you. PCI Slot Function The Peripheral Component Interconnect (PCI) slot is an interface device for the 32-bit computer bus. These tools are integrated on the […]
WHAT IS A RING TOPOLOGY IN A COMPUTER NETWORK?
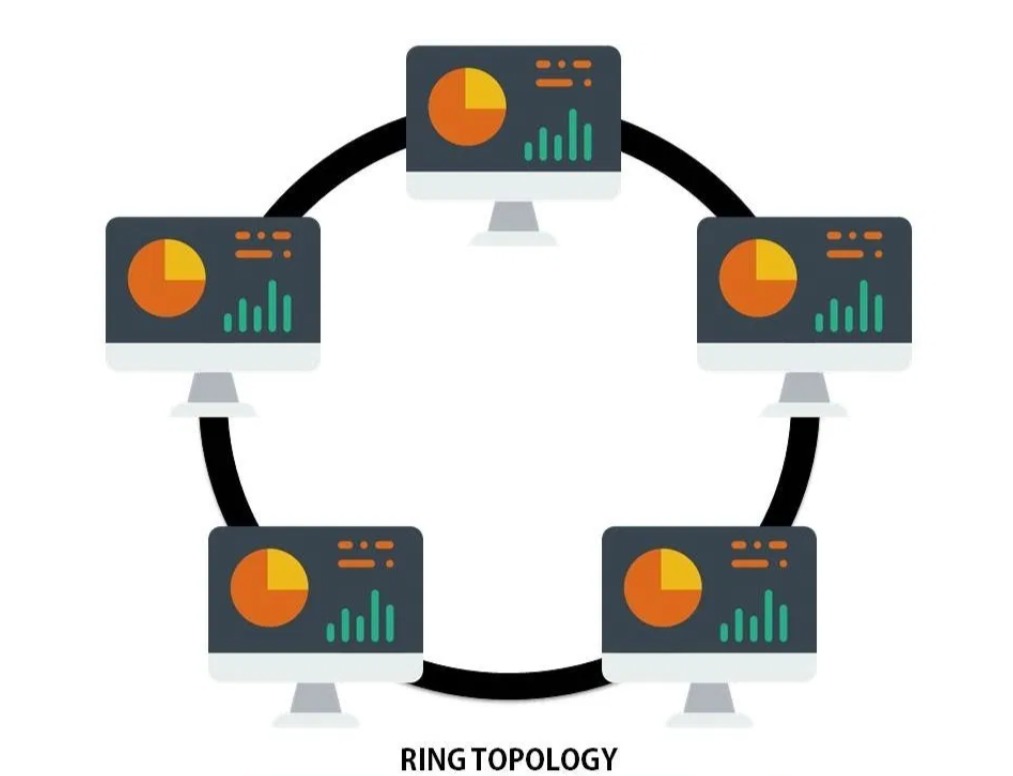
This time Matob will explain what Ring Topology is in a computer network? Accompanied by sample images and their advantages and disadvantages. Topology itself is a branch of mathematics, which is developed from the concept of geometry and set theory, which discusses the unchanging spatial structure in bi-continuous deformations (i.e. space that can be bent, […]
Mcafee: Cyberattacks Target Enterprise Cloud

McAfee found a close link between an increase in attacks on cloud services used by various companies and the increased use of these services due to the digital transformation triggered by the pandemic. Threats also exploit security holes caused by “Shadow IT”, so a new security solution that is capable of detecting them is needed, […]
Should I Pay for Zoom Meetings?
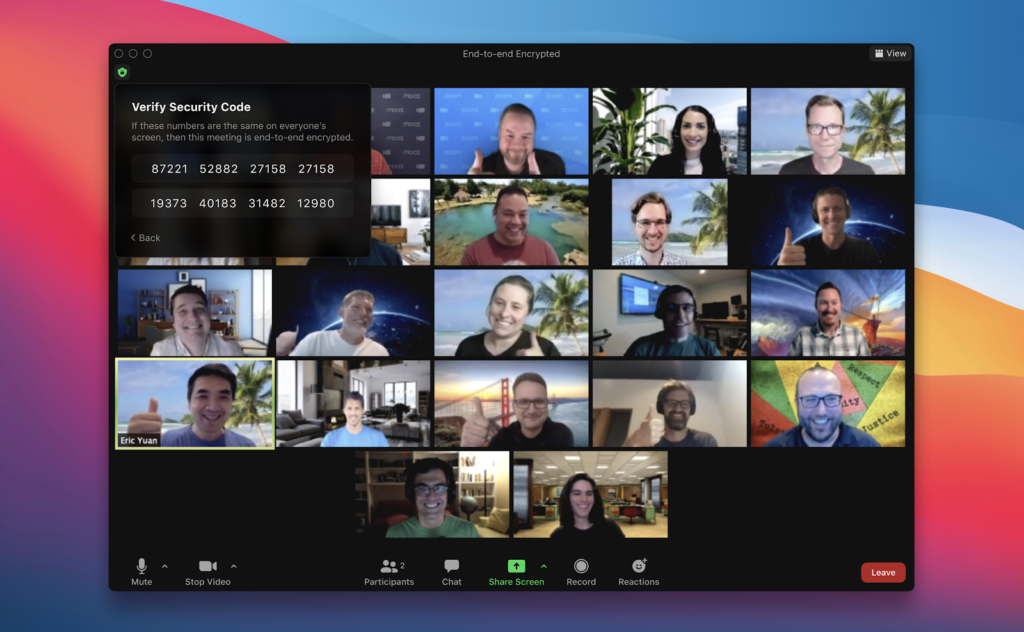
Zoom Meetings has become one of the top video conferencing platforms since the pandemic began. One of the platform’s users is for online education, holding meetings, and even practical methods to keep in touch with family members. Even so, many people may not have a good understanding of what Zoom Meetings are and what they can do. […]
533 Million Facebook User Data Leaked!

A total of 533 million Facebook user data has been leaked. This is based on a report from a user on a low-level hacker forum. It publishes the personal data of hundreds of millions of Facebook users online and for free, making it widely available to anyone with rudimentary data skills. The data revealed included the personal […]
